OWASP Top-Ten: High-Priority Security Risks Every Developer Should Know

Understanding and implementing OWASP Top-Ten helps you address common security vulnerabilities. By applying these security measures, you ensure better protection for your web application against attacks and threats.
Understanding and mitigating fundamental security risks is crucial whether you're building or managing a web application. Security threats to web applications aren't just challenges; they pose serious dangers to user data and information safety. OWASP Top-Ten provides an in-depth view of critical risks that developers and system administrators must recognize and rectify. Let's delve into the details to comprehend each risk and how to prevent them.

Injection
Injection isn't solely a method for attackers to introduce malicious code into your system; it also exploits vulnerabilities in data processing. For instance, SQL injection often occurs when users input strings containing SQL code into search or login fields. This could lead to retrieving user information or even controlling the database.
Prevention Measures:
- Use parameterized queries and prepared statements.
- Thoroughly validate and filter user-inputted data.
- Implement strict data access control mechanisms.
Broken Authentication
When authentication security is compromised, attackers can attempt password guessing, hijack logins, or even expose user personal information.
Example and Prevention:
- Enforce strong passwords and configure limited incorrect login attempts.
- Employ password hashing with robust algorithms like bcrypt or sha-256.
Sensitive Data Exposure
Improperly safeguarded sensitive data can easily be exposed and become a target for attackers.
Remediation:
- Encrypt sensitive data during storage and transmission.
- Use HTTPS protocol for data transmission.
XML External Entities (XXE)
XXE allows attackers to inject malicious XML entities into XML input data, leading to severe consequences like sensitive data retrieval or remote attacks.
Example:
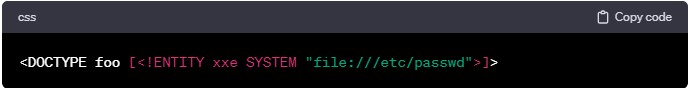
Preventive Measures:
- Disable external entity XML processing or use safer XML processing libraries.
- Inspect and remove unsafe entity declarations from XML input data.
Broken Access Control
This vulnerability enables attackers to access resources or functions they aren't authorized to access.
Example: Users without permission accessing admin pages due to a lack of permission checks.
Prevention Strategies:
- Verify and confirm access rights at the user and role levels.
- Implement strict permission checks and rigorous validation in source code.
Security Misconfiguration
This flaw often occurs when system configurations aren't properly implemented, leaving hidden security vulnerabilities.
Example: Default settings for demo accounts or easily accessible default admin directories.
Preventive Measures:
- Review and eliminate unnecessary demo accounts and sample data.
- Accurately configure security settings while ensuring regular updates.
Cross-Site Scripting (XSS)
XSS is a vulnerability that allows attackers to inject malicious JavaScript into a website to execute on the user's browser.
Example:
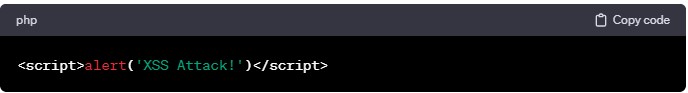
Preventive Measures:
- Use output encoding libraries or escape mechanisms to prevent XSS.
- Thoroughly validate and inspect user-inputted data before displaying it on the website.
Insecure Deserialization
This vulnerability arises when deserializing objects lacks strict control, allowing attackers to inject and execute malicious code.
Example: When deserializing JSON, attackers can inject additional malicious data fields.
Preventive Actions:
- Only deserialize objects from trusted sources.
- Validate and clean data before deserialization.
Using Components with Known Vulnerabilities
This risk occurs when using components with known security vulnerabilities that haven't been patched.
Example: Using an outdated version of a framework with disclosed security flaws.
Preventive Actions:
- Ensure frequent updates for components and frameworks to apply the latest patches.
- Use version control tools to manage and update components.
Insufficient Logging & Monitoring
This risk involves a lack of proper logging measures and monitoring application activities.
Example: Inadequate logging of access or lack of alerts for abnormal activities.
Preventive Measures:
- Maintain comprehensive logs of access, errors, and significant events.
- Set up alerts and notifications for suspicious activities.
OWASP Top-Ten provides an overview of top security risks in web applications and the necessary remediation steps. Ensure that implementing these security solutions will help safeguard your application against potential threats.
related post

Amid the vibrant working atmosphere at Aegona, this September and October will be more exciting than ever with the kickoff of the 2025 Internal Chess Tournament

As scheduled, the monthly internal event “Happy Hour” returned to Aegona’s office this September afternoon, bringing along a joyful atmosphere filled with connection, laughter, and positivity.

Discover the key software outsourcing trends in 2025, from AI, automation, hybrid outsourcing to workforce training. Understanding these trends helps businesses optimize costs and improve software quality.

On June 16, 2025, following a series of technical discussions and alignment on technology directions, Aegona and Biblia officially signed a strategic cooperation agreement to develop a comprehensive digital publishing platform that integrates both E-books and Audiobooks.

In the global software development market, outsourcing Node.js development in Vietnam has become one of the most strategic choices for startups, SMEs, and enterprises looking to optimize costs while maintaining top-notch quality.
We are proud to announce that Aegona has officially achieved ISO 9001:2015 certification, an internationally recognized standard for quality management systems.

Outsourced IT staff offers a strategic alternative: you get skilled professionals exactly when you need them, without the overhead of permanent hires.

Build custom ERP software to streamline operations, boost efficiency, and fit your business needs. A complete step-by-step guide.

Discover the best open-source inventory systems like InvenTree. Learn key features, benefits, and tools to optimize warehouse and inventory operations.

Discover how Tender Management software streamlines bidding, boosts efficiency, and when to choose a custom-built solution.

Discover the benefits of hiring offshore PHP developers in Vietnam and explore a step-by-step process to build a skilled, cost-effective development team.

Discover the key benefits and features of real estate app development in Vietnam for businesses aiming to grow in the digital property market.

Custom FinTech app development for banking, insurance, payments & more. Secure, scalable, and tailored to your business.

Odoo POS software is becoming an effective alternative to traditional POS systems thanks to its flexible integration capabilities and reasonable cost. Using sales management software plays an essential role in optimizing business operations. This article will help you compare Odoo software and traditional POS systems to find the most suitable option for your business.
